
Check Point Application Control Software Blade
The industry's strongest application security and identity control to organizations of all sizes
The Check Point Application Control Software Blade provides the industry's strongest application security and identity control to organizations of all sizes. It enables IT teams to easily create granular policies—based on users or groups—to identify, block or limit usage of over 240,000 Web 2.0 applications and widgets.
*The purchase of a Security Gateway container is required per user
המחיר שלנו: הצעת מחיר
*The purchase of a Security Gateway container is required per user
המחיר שלנו: הצעת מחיר
*The purchase of a Security Gateway container is required per user
המחיר שלנו: הצעת מחיר
מחירים נוספים מופיעים למטה, או לחצו כאן!
שימו לב: כל המחירים באתר כוללים מע"מ. החיוב יבוצע על פי שער "העברות והמחאות מכירה" של המטבע (דולר אמריקאי) ביום אישור ההזמנה.
Benefits:
Granular application control
- Identify, allow, block or limit usage of thousands of applications by user or group
- UserCheck technology alerts users about controls, educates on Web 2.0 risks, policies
- Embrace the power of Web 2.0 Social Technologies and applications while protecting against threats and malware
Largest application library with AppWiki
- Leverages the world's largest application library with over 240,000 Web 2.0 applications and social network widgets
- Identifies, detects, classifies and controls applications for safe use of Web 2.0 social technologies and communications
- Intuitively grouped in over 80 categories—including Web 2.0, IM, P2P, Voice & Video and File Share
Integrated into Check Point Software Blade Architecture
- Centralized management of security policy via a single console
- Activate application control on any Check Point security gateway
Features:
Application detection and usage control
Enables application security policies to identify, allow, block or limit usage (based on bandwidth and/or time) of thousands of applications, including Web 2.0 and social networking, regardless of port, protocol or evasive technique used to traverse the network. Combined with identity awareness capabilities, IT administrators can create very granular policy definitions. User and group application usage is controlled according to user or group needs and applications’ characteristics in terms of security, productivity and resource utilization.
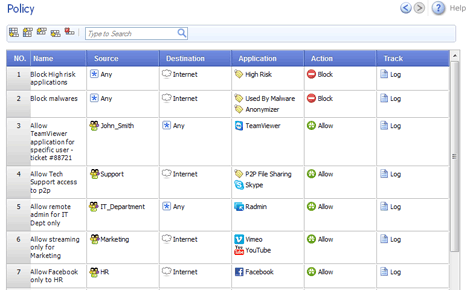
Easily define application-based policies per user or group directly from the firewall.
AppWiki application classification library
AppWikienables application scanning and detection of more than 4,500 distinct applications and over 240,000 Web 2.0 widgets including instant messaging, social networking, video streaming, VoIP, games and more.
Applications are classified into more than 80 categories, based on diverse criteria such as applications’ type, security risk level, resource usage, productivity implications and others. To support the dynamic nature of Internet applications, AppWiki is continuously updated.
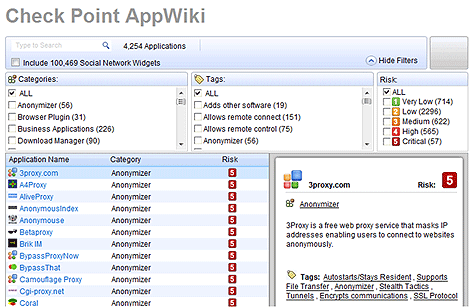
AppWiki: Industry's largest application classification library
Inspect SSL Encrypted Traffic
Scan and secure SSL encrypted traffic passing through the gateway. When traffic is passed through, the gateway decrypts the traffic with the sender’s public key, inspects and protects, then re-encrypts, sending the newly encrypted content to the receiver.
For example, traffic to Facebook may be over HTTP (clear) or HTTPS (encrypted). If the policy blocks usage of Facebook games, it doesn’t matter whether the traffic is encrypted or not – it will be subject to the same policy and blocked.
Granularly define exceptions for SSL inspection to protect user privacy and comply with corporate policy. Some encrypted content passing through the gateway should not be inspected, and therefore can be bypassed with a simple administrator policy definition.
UserCheck
UserCheck technology alerts employees in real-time about their application access limitations, while educating them on Internet risk and corporate usage policies. In addition to defining policies that allow or block specific applications, businesses can choose to query the user by prompting the employee to select whether an application is being used for business or personal use. This enables IT administrators to gain a better understanding of Web 2.0 usage patterns, adapt policies and regulate personal usage without interrupting the flow of business.
User and machine awareness
Integration with the Identity Awareness Software Blade enables users of the Application Control Software Blade to define granular policies to control applications usage by specific users, groups of users and the machine they are using, to best balance between the organization’s security needs and its business needs.
Central policy management
Application Control Software Blades are centrally managed with Check Point security management via a user-friendly interface. Centralized management offers unmatched leverage and control of application security policies and enables organizations to use a single repository for user and group definitions, network objects, access rights and security policies across their entire security infrastructure. Unified access policies are enforced automatically throughout the distributed environment, empowering them to securely provision access from anywhere.
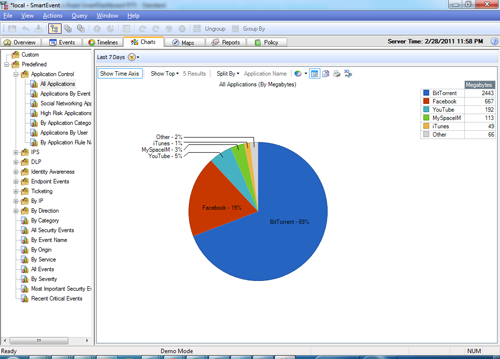
Unified event management
Using SmartEvent to view users’ online behavior and application usage provides organizations with the most granular level of visibility, leading to a better understanding of network usage and the definition of appropriate, granular control policies.
Integrated into Check Point Software Blade Architecture
The Application Control Software Blade is integrated into the Software Blade architecture. It can be easily and rapidly activated on existing Check Point Security Gateways saving time and reducing costs by leveraging existing security infrastructure.
Specifications:
| Supported Appliance Families | |
|---|---|
|
|
| Supported Operating Systems | |
|
הערות תמחור:
- שימו לב: כל המחירים באתר כוללים מע"מ.
- החיוב יבוצע על פי שער "העברות והמחאות מכירה" של המטבע (דולר אמריקאי) ביום אישור ההזמנה.
- מחירי המוצרים וזמינותם כפופים לשינויים ללא הודעה מוקדמת.
*The purchase of a Security Gateway container is required per user
המחיר שלנו: הצעת מחיר
*The purchase of a Security Gateway container is required per user
המחיר שלנו: הצעת מחיר
*The purchase of a Security Gateway container is required per user
המחיר שלנו: הצעת מחיר
*The purchase of a Security Gateway container is required per user
המחיר שלנו: הצעת מחיר
*The purchase of a Security Gateway container is required per user
המחיר שלנו: הצעת מחיר
*The purchase of a Security Gateway container is required per user
המחיר שלנו: הצעת מחיר
*The purchase of a Security Gateway container is required per user
המחיר שלנו: הצעת מחיר
*The purchase of a Security Gateway container is required per user
המחיר שלנו: הצעת מחיר
*The purchase of a Security Gateway container is required per user
המחיר שלנו: הצעת מחיר
*The purchase of a Security Gateway container is required per user
המחיר שלנו: הצעת מחיר
*The purchase of a Security Gateway container is required per user
המחיר שלנו: הצעת מחיר
*The purchase of a Security Gateway container is required per user
המחיר שלנו: הצעת מחיר
*The purchase of a Security Gateway container is required per user
המחיר שלנו: הצעת מחיר
*The purchase of a Security Gateway container is required per user
המחיר שלנו: הצעת מחיר
*The purchase of a Security Gateway container is required per user
המחיר שלנו: הצעת מחיר
*The purchase of a Security Gateway container is required per user
המחיר שלנו: הצעת מחיר
*The purchase of a Security Gateway container is required per user
המחיר שלנו: הצעת מחיר
*The purchase of a Security Gateway container is required per user
המחיר שלנו: הצעת מחיר
*The purchase of a Security Gateway container is required per user
המחיר שלנו: הצעת מחיר
*The purchase of a Security Gateway container is required per user
המחיר שלנו: הצעת מחיר
*The purchase of a Security Gateway container is required per user
המחיר שלנו: הצעת מחיר
*The purchase of a Security Gateway container is required per user
המחיר שלנו: הצעת מחיר
-Up to 50 users
המחיר שלנו: הצעת מחיר
-Up to 500 users
המחיר שלנו: הצעת מחיר
-Unlimited Users
המחיר שלנו: הצעת מחיר
-Unlimited Users
המחיר שלנו: הצעת מחיר
