
Check Point Data Loss Prevention Software Blade
Combines technology and processes to revolutionize Data Loss Prevention
Check Point DLP Software Blade combines technology and processes to revolutionize Data Loss Prevention (DLP), helping businesses to pre-emptively protect sensitive information from unintentional loss, educating users on proper data handling policies and empowering them to remediate incidents in real-time.
*The purchase of a Security Gateway container is required per user
המחיר שלנו: הצעת מחיר
*The purchase of a Security Gateway container is required per user
המחיר שלנו: הצעת מחיר
מחירים נוספים מופיעים למטה, או לחצו כאן!
שימו לב: כל המחירים באתר כוללים מע"מ. החיוב יבוצע על פי שער "העברות והמחאות מכירה" של המטבע (דולר אמריקאי) ביום אישור ההזמנה.
Benefits:
Pre-emptive data loss prevention for critical business information
- UserCheck technology allows for real-time user remediation
- MultiSpect combines users, content and process for unrivaled accuracy
- Educates and alerts users without involving IT/security personnel
- Inspect and control sensitive emails both leaving the organization and between departments
Easy DLP deployment and simplified management
- Centralized management of security policy via a single console
- Pre-configured policies allow for immediate data loss prevention
- Broadest support for file formats and data types
Integrated into Check Point Software Blade Architecture
- Activate DLP on any Check Point security gateway
- Powerful and highly scalable dedicated DLP-1 appliances also available
Features:
Check Point UserCheck
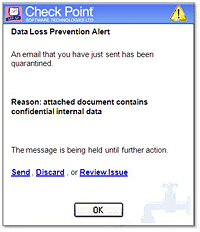
Check Point UserCheck empowers users to remediate incidents in real time. This innovative technology alerts users of suspected breaches for instant remediation and allows quick authorization of legitimate communications.
UserCheck improves security and raises awareness of data use policies by empowering users to self-administer incident handling-with options to send, discard or review the issue. Notifications occur in real-time via a pop-up from a thin agent or via a dedicated email sent to the end-user (no need to install agent).
Organizations benefit in several ways:
- Full prevention - enables a practical move from detection to data loss prevention
- Self-educating system - educates and alerts users without involving IT/security personnel
Protect Against Data Breaches Both Externally and Internally
Check Point DLP controls sensitive information from leaving the company. DLP also inspects and controls sensitive emails between departments with Microsoft Exchange support. An agent is loaded onto the Microsoft Exchange server that intercepts outgoing messages. The message is redirected to the Check Point Gateway, is inspected by the active DLP Software Blade, and then sent to the internal recipient by the Exchange server. Policies can be defined to prevent confidential data from leaking to the wrong departments. Examples of data that might need protecting from accidental leakage to other departments are compensation plans, confidential human resources documents, mergers and acquisition documents, or medical forms.
Inspect SSL Encrypted Traffic
Scan and secure SSL encrypted traffic passing through the gateway. When traffic is passed through, the gateway decrypts the traffic with the sender’s public key, inspects and protects, then re-encrypts, sending the newly encrypted content to the receiver.
For example, Gmail traffic is encrypted over HTTPS. If a user attaches a file to a message in Gmail, both the email and file will be inspected by DLP and be subject to the same policy as any clear (unencrypted) traffic.
Granularly define exceptions for SSL inspection to protect user privacy and comply with corporate policy. Some encrypted content passing through the gateway should not be inspected, and therefore can be bypassed with a simple administrator policy definition.
Check Point MultiSpect
The innovative Check Point MultiSpect data classification engine combines users, content and process into accurate decisions. Check Point DLP delivers exceptionally high accuracy in identifying sensitive data including Personally Identifiable Information (PII), compliance-related data (HIPAA, SOX, PCI, etc.) and confidential business data. This is achieved through the MultiSpect technology, a strong 3-tier inspection engine that:
- Offers multi-parameter data classification and correlation - Multi-protocol inspection and enforcement inspects content flows and enforces policies in the most widely used TCP protocols including: SMTP, FTP, HTTP and webmail. Pattern matching and file classification allows for the identification of content types regardless of the extension applied to the file or compression.
- Recognizes and protects sensitive forms - Includes file/ form matching (based on predefined templates)
- Identifies unconventional business communication behavior
- Leverages out-of-the-box best practice policies
In addition, an open scripting language is available for creating custom data types. This unique flexibility provides virtually unlimited support for protecting sensitive data.
Network-wide Protection Coverage
The Check Point DLP Software Blade is an in-line, advanced data loss prevention solution for data transmitted over networks. It offers wide coverage of traffic transport types, including deep application awareness that protects data in motion, such as SMTP, HTTP and FTP data. DLP policies are created to define what to prevent and how to prevent it, by policy, by network segment, by gateway and by user-group.
Watermarking
The DLP Software Blade has a new document watermark feature in R75.40 that provides additional data protection by dynamically watermarking documents leaving the organization for stronger data security and increased regulatory compliance.
Flexible choice of visible watermarks to Microsoft Office documents:
- Page placement
- Text formatting options such as semitransparent, diagonal, size, font, color, text direction
- Customize watermark with fields such as sender, recipient, name of document and/or date sent
Add encrypted hidden watermarks:
- No change in visible document layout
- Can be identified in DLP scans
- Used for forensics analysis to track leaked documents
Central Policy Management
DLP Software Blades are centrally managed with Check Point security management via a user-friendly interface. Centralized management offers unmatched leverage and control of security policies and enables organizations to use a single repository for user and group definitions, network objects, access rights and security policies across their entire security infrastructure. Unified access policies are enforced automatically throughout the distributed environment, empowering them to securely provision access from anywhere.
Unified policy deployment across multiple gateways controls enforcement actions per policy; i.e. detect (log only), or quarantine (self-incident handling). Policy management includes the following features and options:
- Selection of data type(s) and user group(s) - also using Active Directory
- Enable exceptions - allowed users
- Traffic direction - enforce on outbound or inter-departmental traffic
- Pre-defined policies and content data types
- Incremental exposure of specific policies per different user groups
- Integrated logging and event correlation
- Customization of internal quarantine
- Granular protection control - easy-to-use protection profiles allow administrators to define signature and protection activation rules that match the security needs of their network assets
- Predefined default and recommended profiles - provides immediate and easy out-of-the-box use with profiles tuned to optimize security or performance
Event Management
Separating the needle from the haystack, SmartEvent for DLP monitors and reports only what is important. Event management includes the following features and options:
- Real-time and history graphing and reporting of DLP events
- Easy incident correlation
- Graphical incident timelines
- Easily configured custom views
- Event/incident management workflow
Rapid and Flexible Deployment
Organizations of any size can be protected from the start with pre-configured templates for immediate data loss prevention. A wide range of built-in policies and rules are included for common requirements, including regulatory compliance, intellectual property and acceptable use.
The Check Point DLP Software Blade can be installed on any Check Point security gateway (based on Check Point appliances or open server platforms). Deploy easily and rapidly on existing Check Point security gateways, saving time and reducing costs by leveraging existing security infrastructure. In addition, a full range of powerful and highly scalable DLP-1 Appliances are available to align with any network security requirements.
Integrated into Check Point Software Blade Architecture
The DLP Software Blade is integrated into the Software Blade Architecture. It can be easily and rapidly activated on existing Check
Specifications:
Software Specifications
The DLP Software Blade is a software solution based on the Software Blade architecture. For deployment on open servers, it is tested for compatibility with a wide variety of currently shipping and pre-release hardware platforms.
| Inspection | ||
|
Inspection Options |
|
|
| File Types | Inspection of content for more than 800 file types | |
| Protocols | HTTP, HTTPS, SMTP, FTP | |
| Supported Regulations | PCI-DSS, HIPAA, PII and more | |
|
Non-regulated Data Types |
|
|
| Multi-language Support | Detection of content in multiple languages, including single and double-byte fonts (UTF-8) | |
| Enforcement | ||
| Types |
Ask User (self-prevent with UserCheck) - places message in quarantine, send notification to end-user, request self-remediation Inform User - allow transmission, but notifies user to educate of potential risk |
|
|
UserCheck |
Enabled and customized per policy with individual editable notification to end-user (multi-language) Self-learning - prevents recurring incident management within same mail thread Two notification methods - email reply (no need for agent installation) or system tray pop-up (requires thin agent installation ) |
|
|
Enforcement Features |
Policy exceptions per user, user group, network, protocol or data type Send notification of potential breaches to owner of data asset (e.g., CFO for financial documents) Log all incidents - with option to correlate events and audit incidents |
|
|
View Incident |
An administrator with DLP permissions (a dedicated password) can view the actual message sent, including attachments. An audit log is created each time a message is viewed. You can control whether or not administrators can see all log fields and the captured data itself. You can also control admin's views so they can only see a limited set of incident data. |
|
| Log All Emails | All outgoing emails (including non-incidents) are logged for sender, recipients and subject | |
| Policy Management | ||
| Central Management |
|
|
|
Event Management |
|
|
| Deployment | ||
| Installation Options |
|
|
| Network Deployment Options | Inline connectivity | |
|
Installation Wizard |
Simple wizard that assists in first stage operation of the DLP Software Blade, including connectivity to Active Directory and different initial required configurations | |
| Minimum Hardware Requirements for Installing DLP Software Blade | ||
| Open Server Recommended Requirements |
|
< 5000 users |
| CPU Cores | 2 | 8 |
| RAM Size | 4GB | 4GB |
| Storage Size | 250G | 500G |
| Network Interface Cards (NICs) | 2 | 2 |
Hardware Specifications
| DLP-1 2571 | DLP-1 9571 | |
|---|---|---|
| Software Version | R71, R75, R75.20 | R71, R75, R75.20 |
| Performance | ||
| Number of Users | 1000 | 5000 |
| Messages/Hour | 70,000 | 350,000 |
| Throughput | 700 Mbps | 2.5 Gbps |
| Interfaces | ||
| Built-in Interfaces | 6 Copper 1 GbE | 10 Copper 1 GbE |
| Optional Interfaces | 4-port built-in bypass card (optional) | LOM 2x4 1 GbE Fiber 2x4 1GbE Copper 2x2 10 GbE Modular 4-port, copper, bypass card |
| Storage | ||
| Storage Size | 500GB | 2x1 TB (mirrored - RAID 1) |
| Physical Specifications | ||
| Enclosure | 1U | 2U |
| Dimensions (standard) | 17.4 x 15 x 1.73 in. | 17 x 20 x 3.46 in. |
| Dimensions (metric) | 443 x 381 x 44mm | 431 x 509.5 x 88mm |
| Weight | 6.5 kg (14.3 lbs) | 16.5 kg (36.3 lbs) |
| Power | ||
| Dual, Hot-swappable Power Supplies | No | No |
| Power Input |
100 ~ 240V; 50 ~ 60Hz |
|
| Power Supply Spec (max) | 250W | 400W |
| Power Consumption Spec (max) | 77.5W | 200.7W |
| Operating Environment Range |
Temperature: 5° to 40° C, Humidity: 10%-85% non-condensing, Altitude: 2,500m |
|
| Compliance |
UL 60950; FCC Part 15, Subpart B, Class A; EN 55024; EN 55022; VCCI V-3AS/NZS 3548:1995; CNS 13438 Class A (test passed; country approval pending); KN22KN61000-4 Series, TTA; IC-950; ROHS |
|
| Supported Appliance Families | |
|
|
| Supported Operating Systems | |
|
הערות תמחור:
- שימו לב: כל המחירים באתר כוללים מע"מ.
- החיוב יבוצע על פי שער "העברות והמחאות מכירה" של המטבע (דולר אמריקאי) ביום אישור ההזמנה.
- מחירי המוצרים וזמינותם כפופים לשינויים ללא הודעה מוקדמת.
*The purchase of a Security Gateway container is required per user
המחיר שלנו: הצעת מחיר
*The purchase of a Security Gateway container is required per user
המחיר שלנו: הצעת מחיר
*The purchase of a Security Gateway container is required per user
המחיר שלנו: הצעת מחיר
*The purchase of a Security Gateway container is required per user
המחיר שלנו: הצעת מחיר
*The purchase of a Security Gateway container is required per user
המחיר שלנו: הצעת מחיר
*The purchase of a Security Gateway container is required per user
המחיר שלנו: הצעת מחיר
*The purchase of a Security Gateway container is required per user
המחיר שלנו: הצעת מחיר
*The purchase of a Security Gateway container is required per user
המחיר שלנו: הצעת מחיר
*The purchase of a Security Gateway container is required per user
המחיר שלנו: הצעת מחיר
*The purchase of a Security Gateway container is required per user
המחיר שלנו: הצעת מחיר
*The purchase of a Security Gateway container is required per user
המחיר שלנו: הצעת מחיר
*The purchase of a Security Gateway container is required per user
המחיר שלנו: הצעת מחיר
*The purchase of a Security Gateway container is required per user
המחיר שלנו: הצעת מחיר
*The purchase of a Security Gateway container is required per user
המחיר שלנו: הצעת מחיר
*The purchase of a Security Gateway container is required per user
המחיר שלנו: הצעת מחיר
*The purchase of a Security Gateway container is required per user
המחיר שלנו: הצעת מחיר
-Up to 50 users
המחיר שלנו: הצעת מחיר
-Up to 500 users
המחיר שלנו: הצעת מחיר
-Unlimited Users
המחיר שלנו: הצעת מחיר
-Unlimited Users
המחיר שלנו: הצעת מחיר
