
Check Point Endpoint Security Media Encryption
Prevents data leakage and encrypts removable media
Endpoint Security Software Blades:
- Full Disk Encryption
- Media Encryption
- Remote Access
- Anti-Malware / Program Control
- WebCheck
- Firewall / Compliance Check (included in container purchase)
*The purchase of an Endpoint container is required per user
*Includes 1 year Standard Support.
המחיר שלנו: הצעת מחיר
המחיר שלנו: הצעת מחיר
המחיר שלנו: הצעת מחיר
המחיר שלנו: הצעת מחיר
A Checkpoint User Account number is required to order EndPoint Products.
Please create one here. Please supply the account number in the customer comments.
מחירים נוספים מופיעים למטה, או לחצו כאן!
שימו לב: כל המחירים באתר כוללים מע"מ. החיוב יבוצע על פי שער "העברות והמחאות מכירה" של המטבע (דולר אמריקאי) ביום אישור ההזמנה.
Overview:
The Check Point Media Encryption Software Blade provides centrally-enforceable encryption of removable storage media such as USB flash drives, backup hard drives, CDs and DVDs, for maximum data protection. Port control enables management of all endpoint ports, plus centralized logging of port activity for auditing and compliance.
Comprehensive data protection and control for endpoint removable media
- Encrypt files and folders; track and manage removable devices individually
- Automatic transparent encryption for DVDs and CDs burned with endpoint PCs
- Integrated into Software Blade Architecture for on-demand data security
Maximize operational efficiency with industry-leading performance
- Fast initial and recurring scan times
- Minimal memory usage
Easy-to-use, transparent centralized management from a single console
- Central policy enforcement of removable media and port usage policies
- Central log of media usage and data movement for compliance, forensic analysis
Features & Benefits:
Set Encryption from Centralized Security Management
The centralized endpoint security manager allows administrators to set and enforce encryption policy for removable media and devices using algorithms such as AES 256-bit, for maximum data protection. Unique to Check Point, users can securely access encrypted media from unmanaged computers, with no client installation.
Device Access Settings
The device access settings control access to removable media, devices and ports. Devices can be defined at a granular level by type, brand, size or ID, for maximum data protection. Access to endpoint ports such as USB, FireWire, Bluetooth, WiFi, printer, etc., can be centrally managed.
Removable Media Enforcement
Removable media enforcement maximizes data security by placing a unique digital signature on each encrypted device, informing the user of any unauthorized changes made to stored information. Should any changes be detected, the device will need to be re-authorized before it can be used in the protected environment again.
Logging and Alerts
Administrators can store device activity and file movement logs to a central database, enabling centralized auditing and reporting for easy compliance. Email alerts can be configured to notify administrators about specific events.
Store device activity and file movement logs to a central database
Central Management
The Full Disk Encryption Software Blade is centrally managed by the Endpoint Policy Management Software Blade, enabling central policy administration, enforcement and logging from a single, user-friendly console. The Full Disk Encryption Software Blade is centrally managed by the Endpoint Policy Management Software Blade, enabling central policy administration, enforcement and logging from a single, user-friendly console. Centralized management offers unmatched leverage and control of security policies and multiple deployment options offer easy installation and minimize user impact, for a reduced overall cost of operations.
Integrated into Check Point Software Blade Architecture
The Full Disk Encryption Software Blade is fully integrated into the Software Blade architecture, saving time and reducing costs by allowing customers to quickly expand security protections to meet changing requirements. The Full Disk Encryption Software Blade is integrated into the Software Blade Architecture. Endpoint Security Software Blades from Check Point bring unprecedented flexibility, control and efficiency to the management and deployment of endpoint security. Choose from six Software Blades to deploy only the protection you need, with the freedom to increase security at any time from a single central management console.
Deployment:
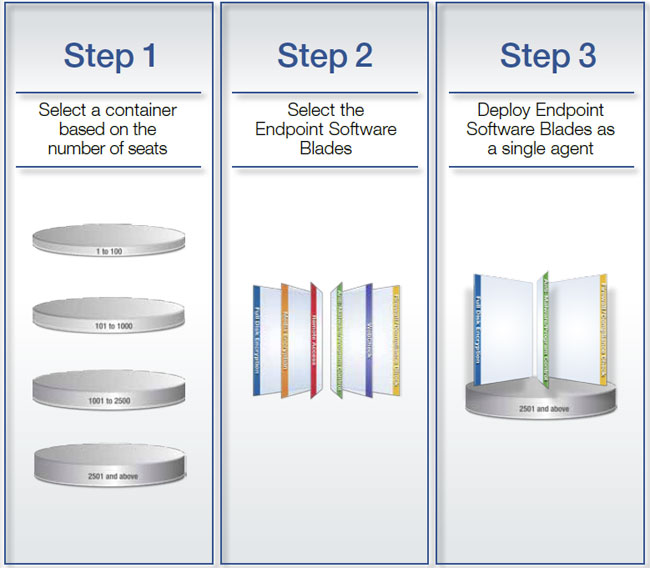
Specifications:
| Client Platform Support: | |
| Operating Systems |
|
| CD/DVD Buring Application Integration: | |
| Applications |
|
| Client Language Support: | |
| Languages |
|
| Certifications: | |
| Media Encryption Certificates |
|
| Ports Controlled: | |
| Port Types | USB, WiFi, Fire Wire, IDE, Bluetooth, PS/2, PCMCIA, SATA, IrDA and SCSI |
| Devices Controlled: | |
| Device Types | USB flash drives, floppy drives, external hard drives, tape drives, Windows Mobile Smartphones, PDAs, imaging devices, scanners, iPhones, Blackberrys, modems, other network access devices, iPods, other digital music devices, printers, CD/DVD drives, keyboard, mouse, digital cameras, wireless network interface cards, biometric devices and smart cardreaders |
Documentation:
Download the Check Point Software Blade Architecture Brochure (PDF).
הערות תמחור:
- שימו לב: כל המחירים באתר כוללים מע"מ.
- החיוב יבוצע על פי שער "העברות והמחאות מכירה" של המטבע (דולר אמריקאי) ביום אישור ההזמנה.
- מחירי המוצרים וזמינותם כפופים לשינויים ללא הודעה מוקדמת.
*The purchase of an Endpoint container is required per user
*Includes 1 year Standard Support.
המחיר שלנו: הצעת מחיר
המחיר שלנו: הצעת מחיר
המחיר שלנו: הצעת מחיר
המחיר שלנו: הצעת מחיר

