
Check Point Identity Awareness Software Blade
The industry's strongest level of gateway security and identity awareness![]()
Check Point Identity Awareness Software Blade provides granular visibility of users, groups and machines, providing unmatched application and access control through the creation of accurate, identity-based policies. Centralized management and monitoring allows for policies to be managed from a single, unified console.
Benefits:
Increases visibility of user activities
- Centrally manage user access to company resources and Internet applications
- Granular user-, group- and machine-based visibility and policy enforcement
- Easily distinguish between employees and others, i.e., guests and contractors
Improves control of corporate resources
- Granular access to data centers, applications and network segments by user, machine or location
- Prevent unauthorized resource access, while allowing users work remotely
- Prevent threats and data loss by restricting access to resources by users and devices
Easy to deploy in any organization
- Integrated into Check Point Software Blade Architecture
- Provides scalable identity sharing between gateways
- Seamless Active Directory (AD) integration with multiple deployment options-Clientless, Captive Portal or Identity Agent
Features:
Configurable Access Roles
The Identity Awareness Software Blade allows you to easily add user, user-group and machine identity intelligence to your security defenses.
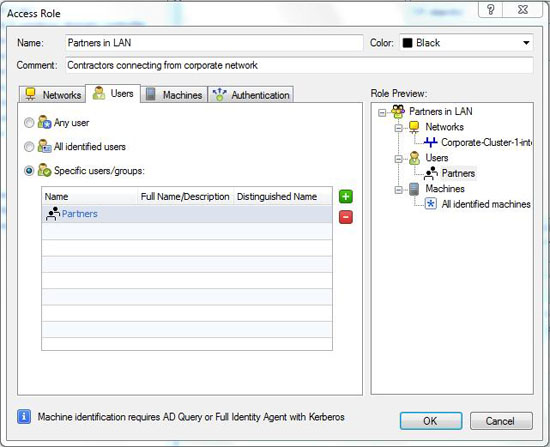
Provide corporate access for specific groups or users leveraging network-wide identity awareness
Multiple User Identification Methods
The Identity Awareness Software Blade provides multiple methods to obtain a user's identity, including: clientless, captive portal or identity agent. Identity information can be used by relevant Software Blades to apply and enforce user-based policies.
- Clientless - This method is easy, fast and simple to deploy. It is based on Active Directory integration and is completely transparent to the user. No installation is required on the Active Directory server or on the client machines.
- Captive portal - This method is used to acquire identities from unidentified users, providing security for endpoints that are not part of the domain. A given user authenticates through a web interface before gaining access to predefined resources for that user profile.
- Identity agent - Identity agents are dedicated client agents installed on users' computers to acquire and report identities to the security gateway. Identity agents give you:
- Transparent authentication using Kerberos Single Sign-On (SSO) when users are logged into the domain
- Added security - the patented packet tagging technology protects from IP spoofing attacks. Identity Agents also give you strong (Kerberos based) user and machine authentication
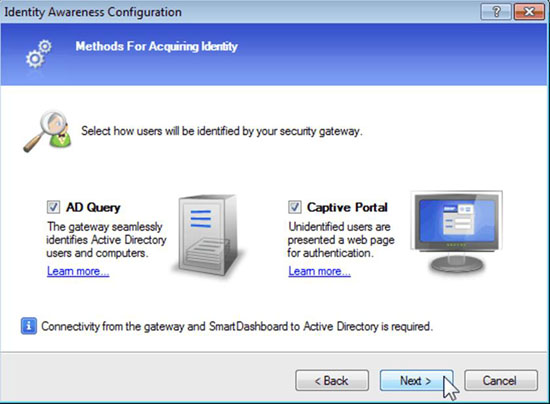
Deployment Wizard
Adding identity intelligence via the Identity Awareness Software Blade is fast and easy with our built-in deployment wizard. In just a few simple steps you can add user, user-group and machine identity awareness and obtain valuable information to utilize in policies throughout your security infrastructure.
Step 1: Provide corporate access for specific groups or users, leveraging network-wide identity awareness.
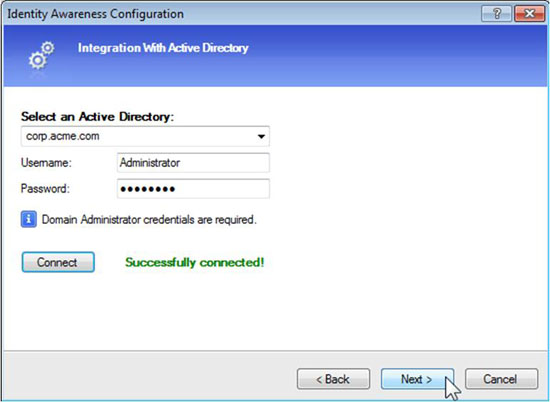
Step 2: Provide your Active Directory credentials for the required domain.
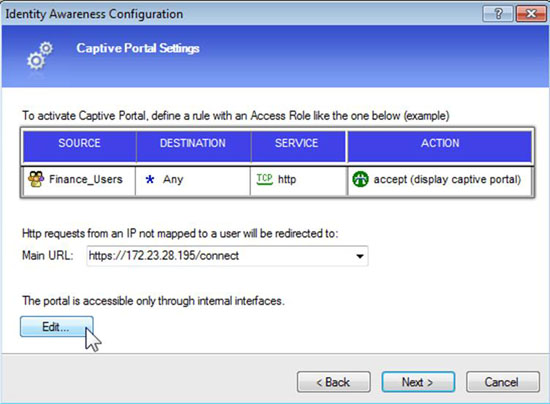
Step 3: Create any rules you require for capturing identity information via the captive portal.
That's all it takes. The Identity Awareness Software Blade will obtaining identity information. If desired, you can change the options that you set in the wizard or deploy other methods, such as identity agents.
Identity Sharing
Identity information can easily be shared, as required, on a single gateway or across the entire network. In a multiple gateway deployment, such as multiple branches or multiple gateways protecting internal resources, identity can be acquired on one gateway and shared amongst all gateways. The benefits of identity sharing include:
- One-time user authentication - user identity is shared between gateways, allowing users to access their defined resources anywhere on the network
- Prevents load on the network from multiple Active Directory lookups
- Simplifies the implementation of Active Directory servers and synchronization
Integrated into Check Point Software Blade Architecture
The Identity Awareness Software Blade is integrated into the Software Blade architecture. It can be easily and rapidly activated on existing Check Point Security Gateways saving time and reducing costs by leveraging existing security infrastructure.
Specifications:
| Supported Appliance Families | |
|
|
| Supported Operating Systems | |
|
|
| Software Blades Interoperation | |
|
|
| Identity Agent Platform Support | |
|
¹IPSO supports identity enforcement and logging. For identity acquisition (AD Query, Captive Portal and Identity Agents), use a SecurePlatform gateway and share the identities with the IPSO gateways. ²Identity Awareness support coming soon
