
Check Point Security Management Software, Pre-defined Systems
Flexible networking and performance options

- Includes a container for managing 1000 Endpoint devices and 3 blades: Endpoint Policy Management, Logging & Status and User Directory.
המחיר שלנו: הצעת מחיר
- Includes a container for managing 2500 Endpoint devices and 3 blades: Endpoint Policy Management, Logging & Status and User Directory.
המחיר שלנו: הצעת מחיר
- Includes a container for managing Unlimited Endpoint devices and 3 blades: Endpoint Policy Management, Logging & Status and User Directory.
המחיר שלנו: הצעת מחיר
- Includes a Security Management container and 3 blades: Network Policy Management, Endpoint Policy Management, Logging & Status.
המחיר שלנו: הצעת מחיר
- Includes a container for Unlimited gateways and 3 blades: Network Policy Management, Endpoint Policy Management, Logging & Status.
המחיר שלנו: הצעת מחיר
- Includes a container for 10 gateways and 7 blades: Network Policy Management, Endpoint Policy Management, Logging & Status, Monitoring, SmartEvent Intro, SmartProvisioning and User Directory.
המחיר שלנו: הצעת מחיר
- Includes a Security Management container and 6 blades: Network Policy Management, Endpoint Policy Management, Logging & Status, Monitoring, SmartEvent Intro and SmartProvisioning.
המחיר שלנו: הצעת מחיר
מחירים נוספים מופיעים למטה, או לחצו כאן!
שימו לב: כל המחירים באתר כוללים מע"מ. החיוב יבוצע על פי שער "העברות והמחאות מכירה" של המטבע (דולר אמריקאי) ביום אישור ההזמנה.
Software Blade Architecture Overview:
Why Software Blade architecture?
Security environments become more complex as companies of all sizes defend themselves against new and varied threats. With these new threats come new security solutions, new vendors, costly new hardware, and increasing complexity. As IT comes under increasing pressure to do more with existing hardware and human resources, this approach becomes increasingly unacceptable.
Check Point's Software Blade architecture offers a better way, enabling organizations to efficiently tailor targeted managed solutions that meet targeted business security needs. All solutions are centrally managed through a single console that reduces complexity and operational overhead. And as new threats emerge, Check Point's Software blade architecture quickly and flexibly expands services as needed without the addition of new hardware or management complexity.
The Check Point Software Blade architecture is the first and only security architecture that delivers total, flexible and manageable security to companies of any size. With this unprecedented capability, Check Point Software Blades deliver lower cost of ownership and cost-efficient protection that meet any network security or endpoint security need, today and in the future.
What is a software blade?
A software blade is a logical security building block that is independent, modular and centrally managed. Software Blades can be quickly enabled and configured into a solution based on specific business needs. And as needs evolve, additional blades can be quickly activated to extend security to an existing configuration within the same hardware foundation.
Key Benefits of the Check Point Software Blade Architecture
- Flexibility – Provides the right level of protection at the right level of investment
- Manageability – Enables fast deployment of security services. Increases productivity through centralized blade management.
- Total Security – Provides the right level of security, at all enforcement points, and at all layers of the network
- Lower TCO - Protects investment through consolidation and use of existing hardware infrastructure
- Guaranteed performance – Enables provisioning of resources that guarantee service levels
How are Check Point Software Blades deployed?
Software Blades can be deployed on Check Point UTM-1 and Power-1 security appliances, open servers, within virtualized environments, and on endpoints. New blades can be added simply by enabling their functionality in software; no additional hardware, firmware or drivers are necessary. This enables organizations to deploy security dynamically, as needed, with lower total cost of deployment.
Getting Started:
Building a security solution using Software Blades
Check Point’s Software Blade Architecture enables customization of tailored systems or quick selection of predefined turnkey solutions.
Tailoring a security gateway or security management solution:
| Step 1: Choose a container | Step 2: Select software blades | Step 3: Configure and deploy |
 |
Security Gateway Blades |
 |
 |
Endpoint Security Blades
|
 |
 |
Security Management Blades
|
 |
Whether designing a solution for corporate headquarters, a data center or a branch office, creating a system takes just three easy steps:
Step 1: Choose a Security Management or Security Gateway Container
Step 2: Select needed Software Blades
Step 3: Configure and Deploy system
The result is a complete gateway or management system configured precisely to a specific business need.
Software Blade Containers
There are three varieties of Software Blade Containers; Security Gateway Containers, Endpoint Security Containers and Security Management Containers. Each Security Gateway Container comes with all of the necessary services required to run the software blade environment along with the Check Point Firewall blade which provides Check Point's patented and award-winning FireWall-1® technology. Each Endpoint Security Container comes with the Firewall / Compliance Check Software Blade.
There are 4 Security Gateway Containers, 4 Endpoint Security Containers and 3 Security Management Containers available:
| Software Blade Containers | ||
|---|---|---|
| Security Gateway Containers | ||
| Name | Cores | Environment |
| SG101 | 1 | Small Office |
| SG201 | 2 | Mid-Size Organizations |
| SG401 | 4 | High Performance |
| SG801 | 8 | Highest Performance |
| Endpoint Security Containers | ||
| Name | Managed Endpoints | Environment |
| CPEP-C1-1TO100 | 1-100 | Small Office |
| CPEP-C1-101TO1000 | 101-1000 | Mid-Size Organizations |
| CPEP-C1-1001TO2500 | 1001-2500 | High Performance |
| CPEP-C1-2501TOU | 2500-Unlimited | Highest Performance |
| Security Management Containers | ||
| Name | Gateways Managed | Environment |
| SM1000 | 10 | Small Companies |
| SM2500 | 25 | Mid-Size Companies |
| SMU000 | Unlimited | Large Enterprises |
Software Blade Container Features
- CoreXL, a patent pending technology delivering near-linear performance scalability (not included in SG101)
- An update service that keeps current with the latest software
- Software blade license management that facilitates blade activation and migration
- SecurePlatform, a pre-hardened operating system that enables quick and easy deployment anywhere in the network
- Web-based administrative interface
- Integrated backup, restore and upgrade capabilities
Endpoint Blades:
Endpoint Security Software Blades from Check Point bring unprecedented flexibility, control and efficiency to the management and deployment of endpoint security. Choose from six Software Blades to deploy only the protection you need, with the freedom to increase security at any time from a single central management console.
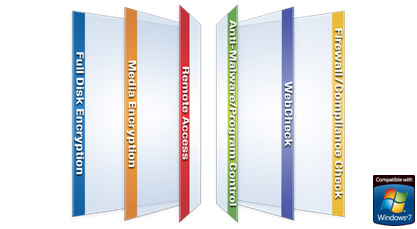
| Endpoint Security Software Blades |
|---|
|
Full Disk Encryption - Automatically and transparently secures all information on endpoint hard drives. Multi-factor pre-boot authentication ensures user identity. Media Encryption - Provides centrally enforceable encryption of removable storage media. Port control enables central management of all endpoint ports, including centralized logging of port activity. Remote Access - Provides users with secure, seamless access to corporate networks and resources when traveling or working remotely. Anti-Malware / Program Control - Efficiently detects and removes malware from endpoints with a single scan. Program Control assures that only legitimate and approved programs run on endpoints. WebCheck - Protects against the latest web-based threats including drive-by downloads, phishing sites and zero-day attacks. Browser sessions run in a secure virtual environment. Firewall / Compliance Check - Proactive protection for inbound and outbound traffic prevent malware from infecting endpoint systems, block targeted attacks and stop unwanted traffic. |
Gateway Blades:
The Check Point Software Blade Architecture supports a complete and increasing selection of Software Blades, each delivering a modular security gateway or security management function. Because Software Blades are modular and moveable, Software Blades enable users to efficiently and quickly tailor Security Gateway and Management functionality to specific and changing security needs. New blades are quickly licensed as needed without the addition of new hardware.
Security Gateway and Security Management blades available today include:
| Security Gateway Software Blades |
|---|
|
Firewall - World's most proven firewall secures more than 200 applications, protocols and services featuring the most adaptive and intelligent inspection technology. IPsec VPN - Secure connectivity for offices and end users via sophisticated but easy to manage Site-to-Site VPN and flexible remote access. Mobile Access - The safe and easy solution to connect to corporate applications over the Internet with Smartphones or PCs. IPS - The highest performing integrated IPS solution with the industry's best threat coverage Application Control - Provides strong application and identity controls by allowing organizations to create policies which identify, block or limit usage of thousands of applications, based on user identity. Identity Awareness - Provides granular security policy at a per user, per group and per machine level. It centralizes the management, monitoring and reporting of user actions across the internal network, its perimeter and beyond. DLP - Combines technology and processes to prevent data loss of critical business information Web Security - Advanced protection for the entire Web environment featuring the strongest protection against buffer-overflow attacks. URL Filtering - Best-of-breed Web filtering covering more than 20 million URLs protects users and enterprises by restricting access to dangerous Web sites. Antivirus & Anti-Malware - Leading antivirus protection including heuristic virus analysis stops viruses, worms and other malware at the gateway Anti-Spam & Email Security - Multi-dimensional protection for the messaging infrastructure stops spam, protects servers and eliminates attacks through email. Advanced Networking - Adds dynamic routing, multicast support and Quality of Service (QOS) to security gateways. Acceleration & Clustering - Patented SecureXL and ClusterXL technologies provide wire speed packet inspection, high availability and load sharing. Voice over IP - Advanced connectivity and security features for VoIP deployments, featuring enhanced Rate Limiting protections, Far end NAT and inspection of SIP TLS. |
| Security Management Software Blades |
|
Network Policy Management - Comprehensive network security policy management for Check Point gateways and blades via SmartDashboard, a single, unified console Endpoint Policy Management - Centrally deploy, manage, monitor and enforce security policy for all endpoint devices across any sized organization. Logging & Status - Comprehensive information in the form of logs and a complete visual picture of changes to gateways, tunnels, remove users and security activities SmartWorkflow - Provides a formal process of policy change management that helps administrators reduce errors and enhance compliance. Monitoring - A complete view of network and security performance, enabling fast response to changes in traffic patterns and security events. Management Portal - Extends a browser-based view of security policies to outside groups such as support staff while maintaining central policy control User Directory - Enables Check Point gateways to leverage LDAP-based user information stores, eliminating the risks associated with manually maintaining and synchronizing redundant data stores. SmartProvisioning - Provides centralized administration and provisioning of Check Point security devices via a single management console. SmartReporter - Turns vast amounts of security and network data into graphical, easy-to-understand reports. SmartEvent - SmartEvent translates security information into action. |
Security Gateway Systems:
To help ease configuration, Check Point has developed several pre-defined bundles composed of a container and software blades.
SG407i
Small offices and branches
- SG103 and SG108 security gateways
- SM1003 and SM1007 security management system.
Medium sized companies and offices
- SG203, SG205i, SG207i and SG209 security gateways
- SM2506 security management
High performance offices of any size
- SG407i and SG409 security gateways
- SM2506, SMU003 and SMU007 security management
Large enterprises, campuses and data centers with demanding performance needs
- SG807 and SG1207 security gateways
- SMU003 and SMU007 security management
Series 100 - An ideal security solution for the small office. A 1 core system, limited to 50 users and recommended up to 8 ports
| Model | Software Blades | Description |
| SG103 | Firewall, VPN, IPS, Application Control, Identity Awareness | An entry level security gateway to provide critical protection the small or branch offices |
| SG108 | Firewall, VPN, IPS, Application Control, Identity Awareness , Anti-Spam & Email Security, URL Filtering, Antivirus & Anti-Malware | An ideal XTM ( eXtensible Threat Management) security gateway providing Total Security for the small and branch office |
Series 200 - A cost-effective security platform for mid-size companies and offices. A 2 core system, limited to 500 users or unlimited users and recommended up to 12 ports.
| Model | Software Blades | Description |
| SG205i | Firewall, VPN, IPS, Application Control, Identity Awareness | An entry level security gateway to provide critical protection for mid-sized companies and offices |
| SG207i | Firewall, IPSEC VPN, IPS, Application Control, Identity Awareness, Advanced Networking, Acceleration & Clustering | High-performance security gateway for mid-sized companies and offices with demanding network environments |
| SG209 | Firewall, VPN, IPS, Application Control, Identity Awareness, Anti-Spam & Email Security, URL Filtering, Antivirus & Anti-Malware, Acceleration & Clustering | Most comprehensive XTM (extensible Threat Management) security gateway with high performance capabilities for mid-sized companies and offices |
Series 400 - Designed for environments that demand high performance. Ideal for the large campus networks and data centers, it is optimized for an 8 core system.It is optimized for 8 core system.
| Model | Software Blades | Description |
| SG407i | Firewall, VPN, IPS, Application Control, Identity Awareness, Advanced Networking, Acceleration & Clustering | High performance security gateway for company of any size |
| SG409 | Firewall, VPN, IPS, Application Control, Identity Awareness, Anti-Spam & Email Security, URL Filtering, Antivirus & Anti-Malware, Acceleration & Clustering | Most comprehensive XTM (eXtensible Threat Management) security gateway for offices of any size requiring high performance |
Series 800 - Designed for the most demanding highest performance environments, the Series 800 security gateway is ideal for the large campus and data center. It is optimized for 8 core system.
| Model | Software Blades | Description |
| SG807 | Firewall, VPN, IPS, Application Control, Identity Awareness, Advanced Networking, Acceleration & Clustering | High-performance security gateway for demanding performance environments. |
Series 1200 - Designed for the most demanding highest performance environments, the Series 800 security gateway is ideal for the large campus and data center. It is optimized for 8 core system.
| Model | Software Blades | Description |
| SG1207 | Firewall, VPN, IPS, Application Control, Identity Awareness, Advanced Networking, Acceleration & Clustering | Highest-performance security gateway for the most demanding performance environments. |
Check Point Security Management Systems:
SM2506

Small offices and branches
- SG103 and SG108 security gateways
- SM1003 and SM1007 security management system.
Medium sized companies and offices
- SG205i, SG205U, SG207i and SG209 security gateways
- SM2506 security management
High performance offices of any size
- SG407i and SG409 security gateways
- SM2506, SMU003 and SMU007 security management
Large enterprises, campuses and data centers with demanding performance needs
- SG807 and SD1207 security gateways
- SMU003 and SMU007 security management
| Model | Software Blades | Description |
| SM1003 | Network Policy Management, Endpoint Policy Management, and Logging and Status | Ideal entry level central security management solution for small organizations. Manages up to 10 gateways |
| SM1007 | Network Policy Management, Endpoint Policy Management, Logging and Status, Monitoring, IPS Event Analysis, SmartProvisioning and User Directory | Ideal entry level central security management solution for small organizations with advanced requirements. Manages up to 10 gateways |
| SM2506 | Network Policy Management, Endpoint Policy Management, Logging and Status, Monitoring, IPS Event Analysis, SmartProvisioning and User Directory | Ideal entry level central security management solution for small organizations with advanced requirements. Manages up to 10 gateways |
| SMU003 | Network Policy Management, Endpoint Policy Management, and Logging and Status | Industry leading central security management solutions for large enterprises. Unlimited number of gateways |
| SMU007 | Network Policy Management, Endpoint Policy Management, Logging and Status, Monitoring, IPS Event Analysis, SmartProvisioning and User Directory | Industry leading central security management solutions for large enterprises with advanced requirements. Unlimited number of gateways |
| Check Point Provider-1 Enterprise Edition Security Management Systems | ||
|---|---|---|
| Model | Software Blades | Description |
| SMV308 | Network Policy Management, Endpoint Policy Management, Logging & Status, Monitoring, IPS Event Analysis, SmartProvisioning, Management Portal and User Directory | Check Point Provider-1 Enterprise Edition brings a highly scalable multi-domain management solution to high-end enterprise customers. That shares global objects and policies across the security domains. Manages up to 3 domains |
| SMV508 | Network Policy Management, Endpoint Policy Management, Logging & Status, Monitoring, IPS Event Analysis, SmartProvisioning, Management Portal and User Directory | Check Point Provider-1 Enterprise Edition brings a highly scalable multi-domain management solution to high-end enterprise customers. That shares global objects and policies across the security domains. Manages up to 5 domains |
Documentation:
Download the Check Point Software Blade Architecture Brochure (PDF).
הערות תמחור:
- שימו לב: כל המחירים באתר כוללים מע"מ.
- החיוב יבוצע על פי שער "העברות והמחאות מכירה" של המטבע (דולר אמריקאי) ביום אישור ההזמנה.
- מחירי המוצרים וזמינותם כפופים לשינויים ללא הודעה מוקדמת.
- A license for these products can be generated for either Software Blades architecture or NGX architecture (Relevant for pre-defined system, Provider-1 Enterprise Edition and Container Expansion products).
- The number of managed gateways can be extended using CPSM-C500.
- SM200, SM300, SM1000, SM2500, SMU000 are licensed to manage 2, 3, 10, 25 and unlimited gateways respectively.
- Customer Log Module (CPSM-P1001) includes a container for 10 gateways and the Logging & Status blade.
- License is per number of managed gateways.
- High Availability configuration of the Security Management requires both primary and secondary servers to have the same container and blade topology. No additional blade (or license) is required beyond this requirement.
- License should be installed on the Security Management Server.
- CPSM-MD1004 includes the NPM, EPM, LOGS and GBLP management blades.
- CPSM-MD1004 can be extended with additional management domains (up to 250 domains).
- Additional management blades (such as SmartProvisioning) added to a multi-domain system apply to all management domains.
- The Multi-Domain log server licenses are additive. CPSM-MLOGS-10 can be extended with additional pre-defined multi-domain log servers (CPSM-MLOGS-10).
- Endpoint Policy Management blade is supported with Endpoint Server version R73.
- Includes a container for managing 1000 Endpoint devices and 3 blades: Endpoint Policy Management, Logging & Status and User Directory.
המחיר שלנו: הצעת מחיר
- Includes a container for managing 2500 Endpoint devices and 3 blades: Endpoint Policy Management, Logging & Status and User Directory.
המחיר שלנו: הצעת מחיר
- Includes a container for managing Unlimited Endpoint devices and 3 blades: Endpoint Policy Management, Logging & Status and User Directory.
המחיר שלנו: הצעת מחיר
- Includes a Security Management container and 3 blades: Network Policy Management, Endpoint Policy Management, Logging & Status.
המחיר שלנו: הצעת מחיר
- Includes a container for Unlimited gateways and 3 blades: Network Policy Management, Endpoint Policy Management, Logging & Status.
המחיר שלנו: הצעת מחיר
- Includes a container for 10 gateways and 7 blades: Network Policy Management, Endpoint Policy Management, Logging & Status, Monitoring, SmartEvent Intro, SmartProvisioning and User Directory.
המחיר שלנו: הצעת מחיר
- Includes a Security Management container and 6 blades: Network Policy Management, Endpoint Policy Management, Logging & Status, Monitoring, SmartEvent Intro and SmartProvisioning.
המחיר שלנו: הצעת מחיר
- Includes a Security Management container and 7 blades: Network Policy Management, Endpoint Policy Management, Logging & Status, Monitoring, SmartEvent Intro, SmartProvisioning and User Directory.
המחיר שלנו: הצעת מחיר
- Includes an Unlimited Container with 4 management blades (NPM, EPM, LOGS, GBLP) and 10 Management Domains (for unlimited gateways)
המחיר שלנו: הצעת מחיר
- Includes 10 Management Domains for Log Server (LOGS)
המחיר שלנו: הצעת מחיר
- Includes Customer Log Module Add-on blade
המחיר שלנו: הצעת מחיר
המחיר שלנו: הצעת מחיר
*The purchase of an Security Management container is required per user
המחיר שלנו: הצעת מחיר
*The purchase of an Security Management container is required per user
המחיר שלנו: הצעת מחיר
*The purchase of an Security Management container is required per user
המחיר שלנו: הצעת מחיר
*The purchase of an Security Management container is required per user
המחיר שלנו: הצעת מחיר
*The purchase of an Security Management container is required per user
המחיר שלנו: הצעת מחיר
*The purchase of an Security Management container is required per user
המחיר שלנו: הצעת מחיר
*The purchase of an Security Management container is required per user
המחיר שלנו: הצעת מחיר
*The purchase of an Security Management container is required per user
המחיר שלנו: הצעת מחיר
