
Check Point Endpoint Security Firewall & Compliance Check
Prevents data leakage and encrypts removable media
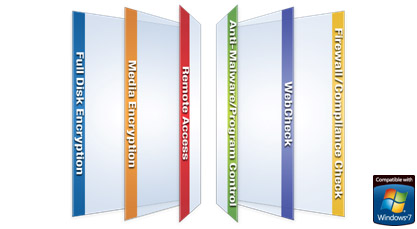
Endpoint Security Software Blades:
- Full Disk Encryption
- Media Encryption
- Remote Access
- Anti-Malware / Program Control
- WebCheck
- Firewall / Compliance Check (included in container purchase)
A Checkpoint User Account number is required to order EndPoint Products.
Please create one here. Please supply the account number in the customer comments.
Overview:
The Check Point Firewall & Compliance Check Software Blade protects endpoints by controlling inbound and outbound traffic and ensuring policy compliance, with centralized management from a single console. Definable zones and security levels protect endpoint systems from unauthorized access. Integrated stealth technology makes endpoints invisible to attackers. This software blade is easily managed by unified Endpoint Security Management.
Comprehensive endpoint security and policy compliance
- Desktop firewall secures endpoints by regulating inbound and outbound traffic
- Centrally definable traffic control, security levels and stealth technology
- Compliance Check ensures that endpoints are in compliance while accessing the corporate network
Integrated into Check Point Software Blade Architecture
- Easily activate endpoint firewall and compliance check on any endpoint
- Flexible licensing options – annual or perpetual
Centrally Managed
- Centrally managed and deployed
- Shared object data base with Network Firewall allows easy setup
Features & Benefits:
Desktop Firewall
The WebCheck Endpoint Software Blade maximizes browser security by virtualizing the browser and creating an isolated protected sandbox for the web browser—thereby segregating corporate data from the Internet. Should a user accidentally visit an infected web site that delivers a drive-by malware download through a browser or if a malicious plug-in is downloaded, no permanent damage will result. Instead, the attack will be contained inside the virtual sandbox and deleted when the browser session ends.
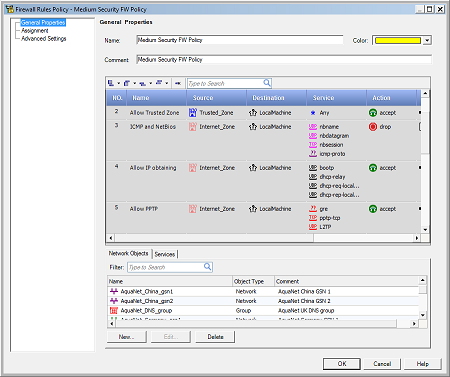
Compliance Check
With compliance scanning, endpoint systems are scanned for compliance with corporate security policy. Systems failing compliance can be directed to remediation.
Administrators can ensure that endpoints are compliant in a number of different areas including:
- Endpoint Security Client software is up-to-date
- Endpoint has the latest authorized Operating System Service Packs
- Check for “blacklisted” applications either running or existing on endpoint
- Check for authorized anti-malware software, versions and DAT updates
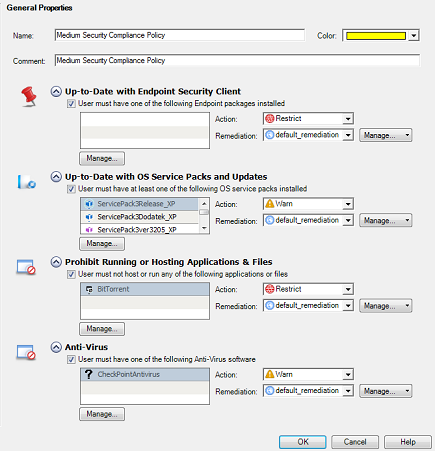
Centralized Management
The Firewall & Compliance Software Blade is centrally managed by the Endpoint Policy Management Software Blade, enabling central policy administration, enforcement and logging from a single, user-friendly console. Centralized management offers unmatched leverage and control of security policies and multiple deployment options offer easy installation and minimize user impact, for a reduced overall cost of operations.
Integrated into Check Point Software Blade Architecture
The Firewall & Compliance Check Software Blade is fully integrated into the Software Blade architecture, saving time and reducing costs by allowing customers to quickly expand security protection to meet changing requirements. Endpoint Security Software Blades from Check Point bring unprecedented flexibility, control and efficiency to the management and deployment of endpoint security. Choose from six Software Blades to deploy only the protection you need, with the freedom to increase security at any time from a single central management console.
Deployment:
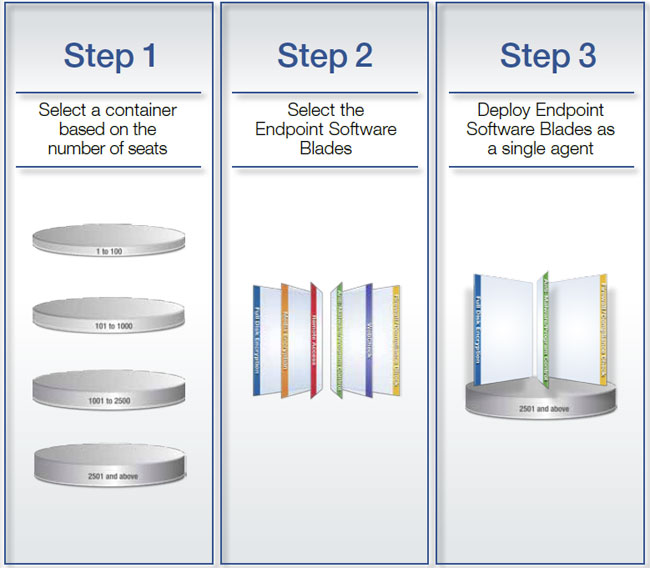
Specifications:
| Compliance Check: | |
| Anti-Malware Vendors and VersionsChecked by Compliance Check | Check Point, Symantec, McAfee, Trend Micro, Kaspersky, Nod32, AVG, Avast, Sophos, Windows Line OneCare, Panda CA, Inoculate IT engine, BitDefender, MS Forefront |
| Firewall Options | |
| Configuration Options | Inbound Firewall, Outbound Firewall, Stealth Mode |
| Platform Support | |
| Operating Systems | Windows 7 (32 & 64 bit), Windows Vista (32 & 64 bit), Windows XP Pro (32-bit, SP2 and later) |
| Client Language Support | |
| Languages | English, Japanese, French, Italian, German, Chinese (simplified), Spanish, Russian |
Documentation:
Download the Check Point Software Blade Architecture Brochure (PDF).
The Firewall/Compliance Check blade is included in your purchase of the endpoint container.

