
Check Point Endpoint Security - Full Disk Encryption
Protecting data where it’s most vulnerable
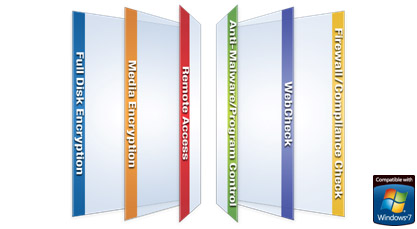
Endpoint Security Software Blades:
- Full Disk Encryption
- Media Encryption
- Remote Access
- Anti-Malware / Program Control
- WebCheck
- Firewall / Compliance Check (included in container purchase)
*The purchase of an Endpoint container is required per user
*Includes 1 year Standard Support.
המחיר שלנו: הצעת מחיר
המחיר שלנו: הצעת מחיר
המחיר שלנו: הצעת מחיר
המחיר שלנו: הצעת מחיר
A Checkpoint User Account number is required to order EndPoint Products.
Please create one here. Please supply the account number in the customer comments.
מחירים נוספים מופיעים למטה, או לחצו כאן!
שימו לב: כל המחירים באתר כוללים מע"מ. החיוב יבוצע על פי שער "העברות והמחאות מכירה" של המטבע (דולר אמריקאי) ביום אישור ההזמנה.
Overview:
The Check Point Full Disk Encryption Software Blade provides automatic security for all information on endpoint hard drives, including user data, operating system files and temporary and erased files. For maximum data protection, multi-factor pre-boot authentication ensures user identity, while encryption prevents data loss from theft.
Comprehensive data protection for endpoint hard drive
- Protects from unauthorized access when laptops are lost or stolen
- Highest security certifications for compliance—FIPS, Common Criteria, BITS
- Comprehensive platform support—including Windows, Mac OS X and Linux
Trusted and proven security for highly-scalable deployments
- Proven in data security deployments of more than 200,000 seats
- Rapid deployment—as fast as 50,000 seats per month
- Nine years as a leader in Gartner Magic Quadrant for Mobile Data Protection
Integrated into Check Point Software Blade Architecture
- Activate endpoint full disk encryption on any Check Point security gateway
- Single-console, centrally-managed endpoint solution
- Supported gateways include: UTM-1, Power-1, IP Appliances, and IAS Appliances
Features & Benefits:
Full Disk Encryption
Automatically encrypts all information on the hard drive - including user data, the operating system, temporary files and erased files, for maximum data protection.
Automatically encrypts all information on the hard drive—including user data, the operating system, temporary files and erased files, for maximum data protection. Logical partitions are boot-protected and encrypted sector-by-sector. Attempts to copy individual files or to introduce rogue programs are blocked, even when the hard drive is removed and slaved to a different computer.
Pre-Boot Authentication
Ensures that only authorized users are allowed to access the endpoint. All valid credentials must be provided before the operating system will boot. Multi-factor authentication options, such as certificate-based Smartcards and dynamic tokens, are supported. Multiple pre-boot authentication languages are supported for global deployments.
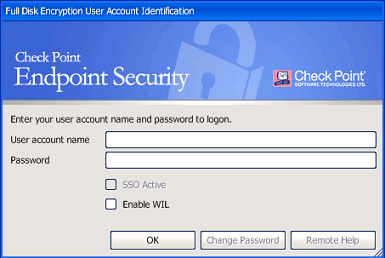
Single-console, Intuitive User Interface
The Full Disk Encryption Endpoint Software Blade provides an intuitive user interface for centralized management and easy viewing of security status and log files or making basic configuration changes.
Multiple client languages are for supported for global deployments.
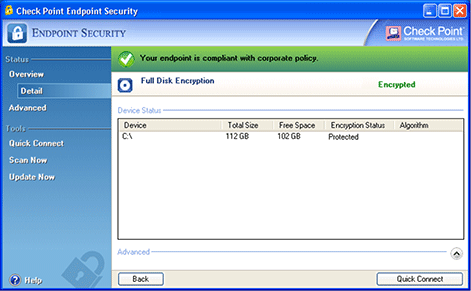
Secure Remote Help
Remote Password Change and One-Time Login remote help options are available for users who may have forgotten their passwords or lost access tokens. Web-based remote help options are available.
Central Management
The Full Disk Encryption Software Blade is centrally managed by the Endpoint Policy Management Software Blade, enabling central policy administration, enforcement and logging from a single, user-friendly console. The Full Disk Encryption Software Blade is centrally managed by the Endpoint Policy Management Software Blade, enabling central policy administration, enforcement and logging from a single, user-friendly console. Centralized management offers unmatched leverage and control of security policies and multiple deployment options offer easy installation and minimize user impact, for a reduced overall cost of operations.
Integrated into Check Point Software Blade Architecture
The Full Disk Encryption Software Blade is fully integrated into the Software Blade architecture, saving time and reducing costs by allowing customers to quickly expand security protections to meet changing requirements. The Full Disk Encryption Software Blade is integrated into the Software Blade Architecture. Endpoint Security Software Blades from Check Point bring unprecedented flexibility, control and efficiency to the management and deployment of endpoint security. Choose from six Software Blades to deploy only the protection you need, with the freedom to increase security at any time from a single central management console.
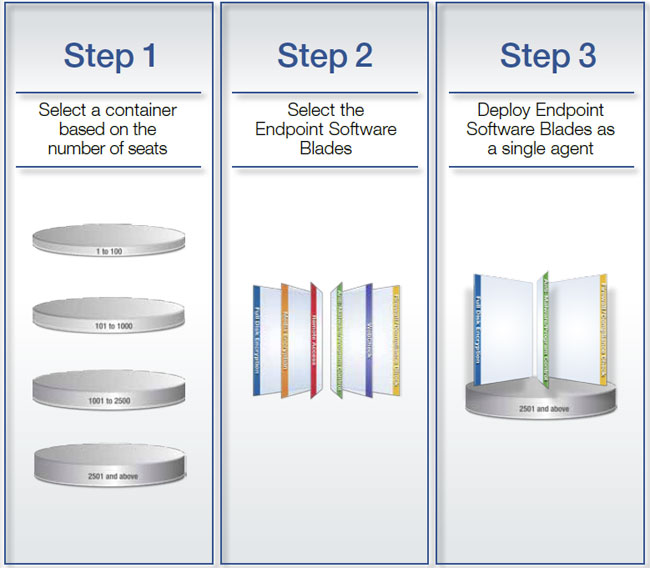
Deployment:
Specifications:
| Client Platform Support: | |
| Operating Systems |
|
| Client Language Support: | |
| Languages |
|
| Pre-Boot Authentication Language Support: | |
| All Client Languages Plus |
|
| Certifications: | |
| Full Disk Encryption |
|
Documentation:
Download the Check Point Software Blade Architecture Brochure (PDF).
הערות תמחור:
- שימו לב: כל המחירים באתר כוללים מע"מ.
- החיוב יבוצע על פי שער "העברות והמחאות מכירה" של המטבע (דולר אמריקאי) ביום אישור ההזמנה.
- מחירי המוצרים וזמינותם כפופים לשינויים ללא הודעה מוקדמת.
*The purchase of an Endpoint container is required per user
*Includes 1 year Standard Support.
המחיר שלנו: הצעת מחיר
המחיר שלנו: הצעת מחיר
המחיר שלנו: הצעת מחיר
המחיר שלנו: הצעת מחיר

