
Check Point Compliance Software Blade
Monitors your management, Software Blades and security gateways

Benefits:
24/7 Security Monitoring Across Check Point Software Blades
- Continually ensures that management, software blades, and security gateways are configured properly
- Highlights poor configuration settings and security weaknesses
- Provides actionable recommendations for security improvements
Real-Time Security Alerts
- Simulates the security impact of configuration changes before installation
- Instant notification on security policy changes negatively impacting security
- Educates users on the broader impact of the desired change
Audit Ready Reports
- Translates thousands of complex regulatory requirements into actionable security best practices
- Delivers real-time assessment of compliance with major regulations
- Compliance Software Blade can be expanded to GRC capabilities with Check Point easy2comply
Features:
Security Best Practices
At the heart of the Compliance Software Blade are hundreds of best practices that define and recommend the optimal configuration for the Check Point Software Blades and management settings. The Compliance Software Blade constantly monitors the compliance status of the organization, enabling network security managers to quickly assess the strength of the current policy settings and where improvements are needed. All best practices have been defined by Check Point security experts
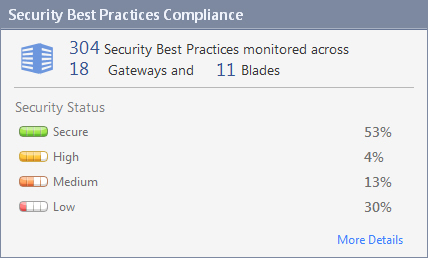
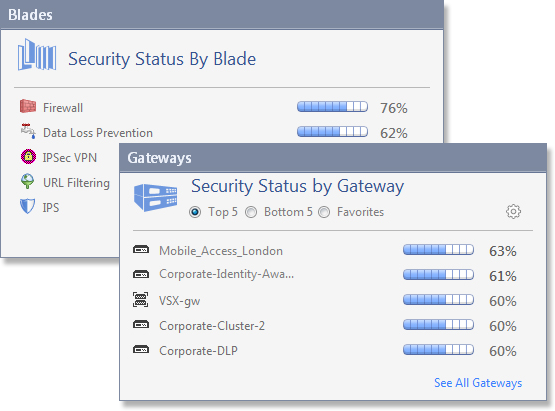
Understand the strength of your security configuration
Monitor the performance of specific gateways and software blades within your network. Security administrators can preform comparisons across the network and see which products are configured properly according to Check Point best practices
Automated Security AlertsAutomatic security alerts are generated by configuration changes to other Check Point Network Security Software Blades, which negatively impact the overall security status. Alerts highlight potential security and compliance violations, reducing the time required and errors associated with manual compliance management. Compliance alerts notify users of the impact of their security decisions and brings regulatory considerations into the forefront of security management.
Integrated into Check Point Software Blade ArchitectureThe Compliance Software Blade is fully integrated into the Check Point Software Blade Architecture. It is the only compliance product that can be automatically and natively implemented with Check Point. The Compliance Software Blade can be easily activated on existing Check Point Security Gateways and Management Servers, saving time and reducing costs by leveraging existing security infrastructure.
Regulatory ComplianceThe Compliance Software Blade provides a clear overview of security compliance position and enables the monitoring of multiple regulations in a single view. Regulations are broken down into the individual requirements and mapped to Check Point’s library of security best practices. As a result, each regulatory requirement is translated into a set of security configuration settings, allowing network security managers to focus on security while improving compliance and providing detailed audit-ready compliance reports with a simple click.
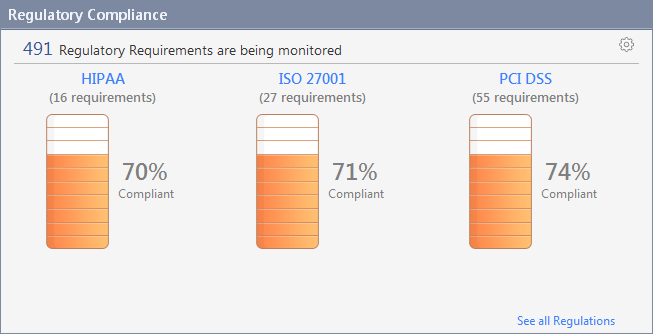
All security best practices have corresponding recommendations, assisting security managers in understanding what actions need to be taken to improve compliance and security. The Compliance Software Blade enables effective management of actions and recommendations, and facilitates the prioritization and scheduling of action items.
Specifications:
Compliance Specifications
| Supported Features | Details |
|---|---|
| Platforms | Management, Multi-Domain Management |
| Opperating Systems | GAiA, SecurePlatform, Windows |
| Versions | R75.40, R75.45, R75.46, R76, R77 |
| Software Blades | Firewall, IPSec VPN, Mobile Access, IPS, Anti-Bot, Anti-Virus, Anti-Spam & Email Security, Identity Awareness, Application Control, URL Filtering and DLP |
Supported Regulations
| ID | Regulation | Description |
|---|---|---|
| 1 | ISO 27001 | International framework for the management of information security |
| 2 | HIPAA | Patient data protection act for healthcare in the U.S.A. |
| 3 | PCI DSS | Global framework for the protection of credit card data |
| 4 | DSD | Australia's top 35 IT security mitigation strategies |
| 5 | GLBA | U.S. regulation related to financial privacy and safeguards |
| 6 | NIST 800-41 | Guidelines on firewalls and firewall policy from NIST |
| 7 | ISO 27002 | Implementation guidelines for each of the 133 control objectives defined within ISO 27001 |
| 8 | NIST 800-53 | Recommended security controls from NIST. Key document for FISMA and FIPS 200 requirements |
| 9 | CobiT 4.1 (IT SOX) | IT goals for ensuring system security. CobiT is also used as the basis for IT SOX compliance |
| 10 | UK Data Protection Act | UK law that governs the protection of personal data |
| 11 | DISA Firewall STIG | Technical paper detailing guidelines to configure firewalls |
| 12 | GPG 13 | Good Practices Guide defines best practices from the UK government |
| 13 | NERC CIP | Cyber security requirements for utility companies in the USA |
| 14 | MAS TRM | Technology Risk Management guidelines for the Monetary Authority of Singapore |
| 15 | SOX | Refers to the IT controls defined in the CobiT framework. The framework supports governance of IT by defining and aligning business goals with IT goals and IT processes |
| 16 | FIPS 200 | A requirement under FISMA that requires Federal organizations to comply with the Recommended Security Controls specified in NIST 800-53 |
| 17 | APP | The Australian Privacy Principles (APPs) replace the National Privacy Principles and Information Privacy Principles and apply to organisations, and Australian, ACT and Norfolk Island Government agencies. The APPs reference here are taken from Schedule 1 of the Privacy Amendment (Enhancing Privacy Protection) Act 2012, which amends the Privacy Act 1988. |
| 18 | CJIS | CJIS is the Criminal Justice Information Services Security Policy. The essential premise of the CJIS Security Policy is to provide appropriate controls to protect the full lifecycle of CJI, whether at rest or in transit. CJIS is divided into 12 individual policy areas. The controls listed here are referenced in Version 5.2, dated 08/09/2013. |
| 19 | Katakri | Katakri 3.0 refers to the Finnish National Security Authority's National Security Auditing Criteria. Katakri is divided into four sub-divisions: Administrative, Personnel, Physical, and Information Assurance. The mapping provided by Check Point has focused on Information Assurance. Katakri provides different levels of security requirements. The Check Point Katakri mapping is based on 'Requirements for the base level (IV)'. |
| 20 | PPG234 | This prudential practice guide (PPG) aims to assist regulated institutions in the management of security risk in information and information technology (IT). It is designed to provide guidance to senior management, risk management and IT security specialists (management and operational). |
| 21 | POPI | The Protection of Personal Information Act, 2013, is an official act of the Republic of South African parliament. This report refers specifically to Chapter 3 (Conditions for Lawful Processing of Personal Information), and more specifically Condition 7.19, Security Safeguards - Security measures on integrity and confidentiality of personal information. |
| 22 | Statement of Controls | This report identifies the core control requirements of the Check Point Security Management, Security Gateways and Software Blades. All relevant security best practices have been mapped in line with Check Point recommendations. This report allows Check Point users to verify the status of their Check Point security environment and to ensure that it is in line with Check Point's recommendations. |
| 23 | CIPA | The Children's Internet Protection Act (CIPA) place restrictions on the use of funding that is available through the Library Services and Technology Act, Title III of the Elementary and Secondary Education Act, and on the Universal Service discount program known as the E-rate (Public Law 106-554). These restrictions take the form of requirements for Internet safety policies and technology which blocks or filters certain material from being accessed through the Internet. |
| 24 | N-CIPA | The Neighborhood Children's Internet Protection Act (NCIPA) place restrictions on the use of funding that is available through the Library Services and Technology Act, Title III of the Elementary and Secondary Education Act, and on the Universal Service discount program known as the E-rate (Public Law 106-554). These restrictions take the form of requirements for Internet safety policies and technology which blocks or filters certain material from being accessed through the Internet. |
