
Check Point Endpoint Security Remote Access VPN
Prevents data leakage and encrypts removable media
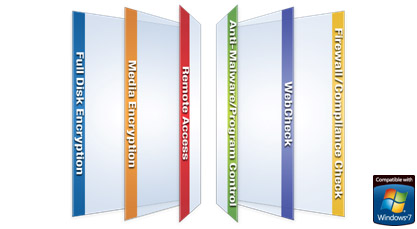
Endpoint Security Software Blades:
- Full Disk Encryption
- Media Encryption
- Remote Access
- Anti-Malware / Program Control
- WebCheck
- Firewall / Compliance Check (included in container purchase)
*The purchase of an Endpoint container is required per user
*Includes 1 year Standard Support
המחיר שלנו: הצעת מחיר
המחיר שלנו: הצעת מחיר
המחיר שלנו: הצעת מחיר
המחיר שלנו: הצעת מחיר
A Checkpoint User Account number is required to order EndPoint Products.
Please create one here. Please supply the account number in the customer comments.
מחירים נוספים מופיעים למטה, או לחצו כאן!
שימו לב: כל המחירים באתר כוללים מע"מ. החיוב יבוצע על פי שער "העברות והמחאות מכירה" של המטבע (דולר אמריקאי) ביום אישור ההזמנה.
Overview:
The Check Point Remote Access VPN Software Blade provides users with secure, seamless access to corporate networks and resources when traveling or working remotely. Privacy and integrity of sensitive information is ensured through multi-factor authentication, endpoint system compliance scanning and encryption of all transmitted data.
Secure access to corporate resources while traveling or working remotely
- Full IPsec VPN connectivity for strong authentication and data integrity
- Endpoint compliance scanning protects from malware and intrusions
Simple user experience
- Seamless roaming between networks and automatic session configuration
- Re-establishes lost connections by automatically switching connection modes
Integrated into Check Point Software Blade Architecture
- Activate endpoint remote access protection on any Check Point gateway
- Centrally-managed endpoint solution
- Supported gateways include: UTM-1, Power-1, IP Appliances, and IAS Appliances
Features & Benefits:
VPN Auto-Connect
VPN auto-connect re-establishes lost connections by automatically switching connection modes. It eliminates the need for users to re-authenticate when roaming between different network types (LAN, WiFi, GPRS, etc.), using intermittent networks or resuming work from sleep mode.
IPsec VPN
Check Point Remote Access Software Blades support full IPsec VPN connectivity for strong authentication, data integrity and confidentiality. NAT-T standard support enables traversing between static and dynamic Network Address Translation (NAT) devices.
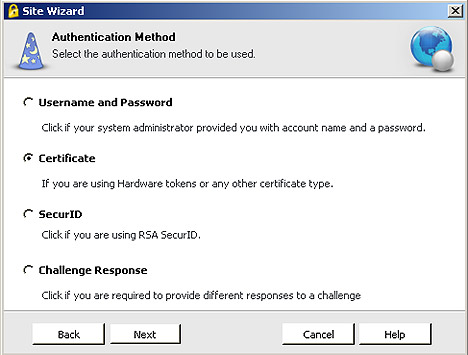
Multi-Factor Authentication Support
The Remote Access Software Blade offers comprehensive authentication, including:
- Username and passwords (including cached passwords)
- SecurID
- Challenge / Response
- CAPI software and hardware tokens
Compliance Scanning
With compliance scanning, endpoints are automatically scanned for malware and suspicious activity to ensure compliance with corporate security policies. Failing endpoints can be directed to remediation.
As an example, administrators can ensure that endpoints are free of malware and have the latest service packs installed before granting access to corporate resources.
Secure Hotspot Registration
With secure hotspot registration, administrators can selectively grant access to hotspot registration sites. Hotspot registration pages are loaded automatically for the user.
Central Management
The Remote Access Software Blade is centrally managed by the Endpoint Policy Management Software Blade, enabling central policy administration, enforcement and logging from a single, user-friendly console. Centralized management offers unmatched leverage and control of security policies and multiple deployment options offer easy installation and minimize user impact, for a reduced overall cost of operations.
Integrated into Check Point Software Blade Architecture
The Remote Access Software Blade is integrated into the Software Blade Architecture. Endpoint Security Software Blades from Check Point bring unprecedented flexibility, control and efficiency to the management and deployment of endpoint security. Choose from six Software Blades to deploy only the protection you need, with the freedom to increase security at any time from a single central management console.
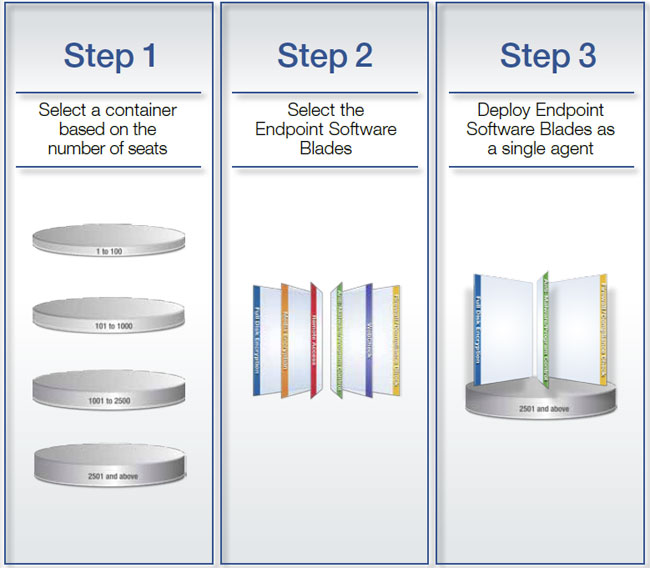
Deployment:
Specifications:
| Client Platform Support: | |
| Operating Systems |
|
| Client Language Support: | |
| Languages |
|
| Gateway Support: | |
| Check Point Gateways |
|
Documentation:
Download the Check Point Software Blade Architecture Brochure (PDF).
הערות תמחור:
- שימו לב: כל המחירים באתר כוללים מע"מ.
- החיוב יבוצע על פי שער "העברות והמחאות מכירה" של המטבע (דולר אמריקאי) ביום אישור ההזמנה.
- מחירי המוצרים וזמינותם כפופים לשינויים ללא הודעה מוקדמת.
*The purchase of an Endpoint container is required per user
*Includes 1 year Standard Support
המחיר שלנו: הצעת מחיר
המחיר שלנו: הצעת מחיר
המחיר שלנו: הצעת מחיר
המחיר שלנו: הצעת מחיר

